Vigenère Cipher: Advanced Polyalphabetic Encryption Tool
This encryption method builds on Caesar cipher principles but takes security to the next level. It uses a keyword to shift each letter by varying amounts based on the repeating keyword pattern, making it far more resistant to basic code-breaking techniques than simple substitution ciphers.
Operation Mode
Keyword
Key Analysis
Input Text
Output Result
Enter keyword and text to see results
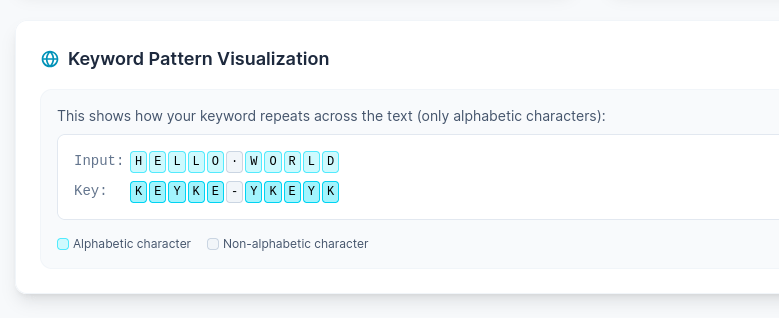
Keyword Pattern Visualization
Encryption Statistics
What is the Vigenère Cipher?
The Vigenère Cipher encrypts alphabetic text by weaving together multiple Caesar ciphers based on a keyword. Known as a polyalphabetic substitution cipher, it employs several different substitution alphabets rather than just one, which makes it substantially more secure than monoalphabetic ciphers like Caesar.
Here's how it works with the keyword "KEY":
- First letter: shifts by K (position 10)
- Second letter: shifts by E (position 4)
- Third letter: shifts by Y (position 24)
- Fourth letter: shifts by K again, and so on...
The keyword cycles through the entire message, building a complex encryption pattern that's tough to crack.
Features of Our Vigenère Cipher Tool:
- Real-time encryption/decryption - See results as you type
- Custom keyword support - Use any word or phrase as your encryption key
- Visual keyword pattern display - See how your keyword repeats across the text
- Case preservation - Maintains original capitalization
- Non-alphabetic character handling - Punctuation and numbers remain unchanged
- Keyword analysis - View key statistics and patterns
- 100% client-side processing - Your data never leaves your browser
- Mobile-responsive design - Works perfectly on all devices
How to Use the Vigenère Cipher Tool
1. Choose Your Operation
Pick "Encrypt" to encode your message or "Decrypt" to reveal an encrypted one. Remember to use the same keyword for both encrypting and decrypting.
2. Enter Your Keyword
Select a keyword that shapes your encryption pattern. Longer keywords with diverse letters offer stronger security. Stay away from repeating patterns or common words when handling sensitive information.
3. Input Your Text
Type or paste whatever text you want to process. The tool instantly encrypts or decrypts it while showing you exactly how the keyword applies to each character.
4. Analyze the Results
Check out the processed text and explore the keyword pattern visualization to see how the cipher operates behind the scenes.
Practical Examples of Vigenère Cipher
| Original Text | Keyword | Encrypted Text |
|---|---|---|
| HELLO WORLD | KEY | RIJVS UYVJN |
| ATTACK AT DAWN | LEMON | LXFOPV EF RNHR |
| CRYPTOGRAPHY | CIPHER | ELCAAEMJZRPJ |
History and Security of the Vigenère Cipher
Giovan Battista Bellaso first described the Vigenère Cipher in 1553, though it was later mistakenly credited to Blaise de Vigenère. For roughly 300 years, cryptographers believed it couldn't be cracked, earning it the nickname "le chiffre indéchiffrable" (the indecipherable cipher).
The cipher gains its strength from employing multiple substitution alphabets:
- Each letter encrypts differently based on where it appears in the message
- Simple frequency analysis becomes far more challenging
- Longer keywords create stronger encryption
- Random or pseudo-random keywords deliver the best security
Despite its historical reputation, modern techniques like Kasiski examination or index of coincidence analysis can crack the cipher, particularly when keywords are short or messages are lengthy.
Advantages and Disadvantages
Advantages
- Far more secure than single-alphabet ciphers
- Resists basic frequency analysis attacks
- Simple to implement and understand
- Works without any special tools
- Can be performed manually with some practice
- Security scales up with keyword length
Disadvantages
- Breaks down with enough encrypted text
- Susceptible to Kasiski examination
- Short keywords dramatically weaken security
- Needs secure way to share keywords
- Inadequate for protecting modern sensitive data
- Repeating keywords leave detectable patterns
Modern Uses for Vigenère Cipher
While it's not suitable for protecting sensitive information today, the Vigenère Cipher still finds use in several areas:
- Teaching advanced cryptography concepts in educational settings
- Creating puzzles and recreational cryptography challenges
- Practicing historical cryptanalysis and code-breaking skills
- Adding encryption elements to games and alternate reality games (ARGs)
- Lightly obscuring non-sensitive data
- Incorporating into steganography projects
- Supporting academic research and cryptographic studies
Security Notice: Though stronger than basic substitution ciphers, the Vigenère Cipher isn't appropriate for protecting sensitive or confidential information in today's applications.
Related Encryption Methods
If the Vigenère Cipher interests you, check out these related cryptographic techniques:
Caesar Cipher
The building block of Vigenère—master single-shift substitution before moving up to polyalphabetic methods.
Try our Caesar Cipher tool →Autokey Cipher
An enhanced version of Vigenère that incorporates the plaintext itself into the key, removing key repetition issues.
Try our Autokey Cipher tool →Frequently Asked Questions
How secure is the Vigenère Cipher?
The Vigenère Cipher beats simple substitution ciphers by a wide margin, but modern cryptanalytic methods can still break it—especially with short keywords or long messages. Don't rely on it for protecting sensitive information.
What makes a good keyword for Vigenère Cipher?
A strong keyword should be lengthy, contain diverse letters, steer clear of repetitive patterns, and avoid common words or phrases. Random character sequences offer the best security, though they're trickier to remember.
Can I use spaces and punctuation in my keyword?
Our tool works with alphabetic characters only for keywords. Spaces and punctuation in your original text stay untouched—only letters get encrypted.
How is Vigenère different from Caesar Cipher?
Caesar Cipher applies one fixed shift to every letter, while Vigenère switches up the shift based on a repeating keyword. This variation makes Vigenère far more resilient against frequency analysis attacks.
Does your tool store my text or keywords?
Not at all. Our Vigenère Cipher tool runs completely in your browser using JavaScript. Your text and keywords never touch our servers, guaranteeing total privacy.
Breaking the Vigenère Cipher
Though far more secure than single-alphabet ciphers, the Vigenère Cipher can still be cracked using several techniques:
1. Kasiski Examination
This technique searches for repeating sequences in the encrypted text—sequences that probably represent identical plaintext encrypted with the same portion of the key. By measuring the distances between these repetitions, you can figure out the key length.
2. Index of Coincidence
This statistical approach examines how letters are distributed throughout the ciphertext to estimate the key length, then applies frequency analysis to each position separately.
3. Friedman Test
A mathematical technique that calculates the probable key length by comparing the coincidence rate in the ciphertext against expected values for various key lengths.