MD5 Hash Generator & Verifier Tool
Generate MD5 hashes for text input or verify existing hashes. MD5 produces a 128-bit hash value, commonly used for file checksums and data integrity verification. Note: MD5 is cryptographically insecure and should not be used for security purposes.
Operation Mode
MD5 Algorithm Info
Input Text
MD5 Hash
Enter text to generate MD5 hash
Hash Statistics
Quick Examples
Security Notice
MD5 is cryptographically broken and unsuitable for security applications. It should only be used for checksums and file verification.
What is MD5?
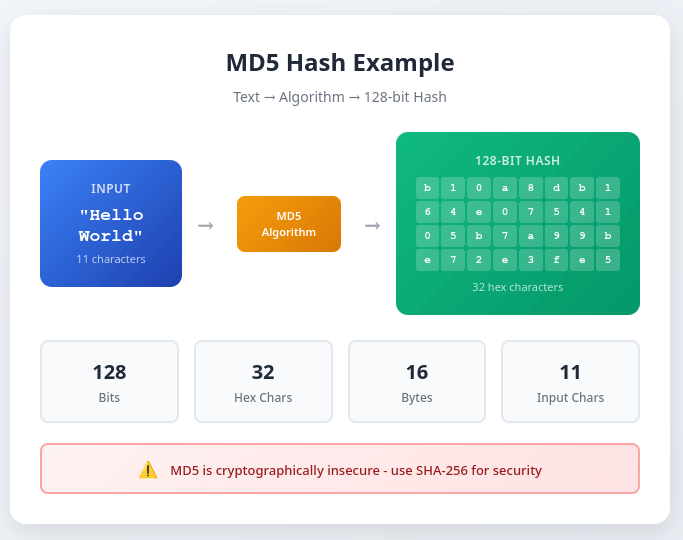
MD5 (Message Digest Algorithm 5) is a cryptographic hash function that produces a 128-bit hash value, typically represented as a 32-character hexadecimal string. Despite being widely used for checksums and file verification, MD5 is cryptographically broken and unsuitable for security applications.
Key characteristics of MD5:
- 128-bit output: Always produces 32 hex characters
- Deterministic: Same input = same hash
- Fast computation: Quick to calculate
- One-way function: Cannot reverse to original
- Collision vulnerable: Same hash for different inputs
Example: "Hello" → "8b1a9953c4611296a827abf8c47804d7"
⚠️ Security Warning
MD5 is cryptographically broken and should not be used for security purposes:
- Collision attacks: Different inputs can produce the same hash
- Rainbow tables: Pre-computed hash databases exist
- Password vulnerability: Not secure for password storage
- Digital signatures: Not suitable for authentication
Use SHA-256 or SHA-512 for security applications instead.
Features of Our MD5 Tool:
- Instant generation - Real-time MD5 hash calculation
- Hash verification - Compare generated vs expected hashes
- Security warnings - Clear information about MD5 vulnerabilities
- File checksum validation - Verify file integrity
- Detailed statistics - Input/output length and bit information
- Copy functionality - Easy hash copying for external use
- Educational examples - Common text hash demonstrations
- Alternative recommendations - Guidance for secure hash functions
How to Use the MD5 Hash Tool
1. Choose Operation Mode
Select "Generate Hash" to create MD5 hashes from text, or "Verify Hash" to compare a generated hash against an expected value.
2. Enter Your Input
Type or paste your text in the input field. The MD5 hash will be generated automatically as you type.
3. Copy or Verify Results
Copy the generated hash for use elsewhere, or paste an expected hash in verification mode to check if they match.
4. Review Statistics
Check the statistics panel for information about input length, hash characteristics, and security considerations.
MD5 Hash Examples
| Input | MD5 Hash | Use Case |
|---|---|---|
| Empty String | d41d8cd98f00b204e9800998ecf8427e | Default/empty file check |
| Hello World | b10a8db164e0754105b7a99be72e3fe5 | Testing and examples |
| password123 | 482c811da5d5b4bc6d497ffa98491e38 | ⚠️ Insecure password hash |
| The quick brown fox... | 9e107d9d372bb6826bd81d3542a419d6 | Standard test string |
Security Considerations
Why MD5 is Insecure
Collision Vulnerabilities
MD5 is susceptible to collision attacks where different inputs produce the same hash. This was mathematically proven in 2004.
Pre-image Attacks
While full pre-image attacks are still difficult, partial attacks exist that can find inputs producing specific hash patterns.
Rainbow Table Attacks
Large databases of pre-computed MD5 hashes exist, making it easy to reverse common passwords and phrases.
Legitimate Uses for MD5
Despite security limitations, MD5 still has valid non-security applications:
- File Checksums - Detecting file corruption or changes
- Data Deduplication - Identifying duplicate files
- Cache Keys - Creating unique identifiers for caching
- ETags - HTTP entity tags for web caching
- Non-cryptographic IDs - Generating unique identifiers
- Legacy System Support - Maintaining compatibility
- Educational Purposes - Learning about hash functions
Secure Alternatives to MD5
For General Hashing
Use for digital signatures, certificates, and general cryptographic purposes
For Password Hashing
Use for storing passwords with automatic salt generation
Hash Function Best Practices
Security Guidelines
✅ Do:
- • Use SHA-256 or SHA-512 for security
- • Add salt to password hashes
- • Use bcrypt/scrypt for passwords
- • Verify file integrity with checksums
- • Use HMAC for message authentication
❌ Don't:
- • Use MD5 for passwords or security
- • Store passwords without salt
- • Trust MD5 for digital signatures
- • Use MD5 for certificate validation
- • Rely on MD5 for cryptographic proof
File Verification with MD5
While MD5 shouldn't be used for security, it's still common for file integrity checks:
Related Hash Tools
Explore these more secure hashing alternatives:
SHA-256 Hash Generator
Generate cryptographically secure SHA-256 hashes suitable for security applications.
Try our SHA-256 tool →bcrypt Password Hasher
Securely hash passwords using bcrypt with automatic salt generation and work factor control.
Try our bcrypt tool →SHA-512 Hash Generator
Generate high-security SHA-512 hashes with 512-bit output for maximum security.
Try our SHA-512 tool →SHA-1 Hash Generator
Generate SHA-1 hashes for legacy systems (also deprecated for security use).
Try our SHA-1 tool →Frequently Asked Questions
Is MD5 still safe to use?
MD5 is not safe for security purposes due to collision vulnerabilities discovered in 2004. However, it's still acceptable for non-security uses like file checksums and data deduplication.
Can I reverse an MD5 hash?
MD5 is designed to be a one-way function, but due to its cryptographic weaknesses and the existence of rainbow tables, many common MD5 hashes can be "reversed" by lookup tables.
Why do different inputs sometimes produce the same MD5 hash?
This is called a collision. MD5's 128-bit output space means collisions are mathematically inevitable (pigeonhole principle), but MD5's specific vulnerabilities make finding collisions much easier than it should be.
What should I use instead of MD5 for passwords?
Use bcrypt, scrypt, or Argon2 for password hashing. These algorithms are specifically designed for passwords and include automatic salt generation and adjustable work factors.
Are MD5 checksums still useful for file verification?
Yes, for detecting accidental file corruption or changes, MD5 checksums are still widely used. However, for security-critical file verification, use SHA-256 or SHA-512.
How long is an MD5 hash?
MD5 always produces a 128-bit hash, which is typically represented as a 32-character hexadecimal string (4 bits per hex character: 32 × 4 = 128 bits).
Technical Implementation
Our MD5 tool uses a JavaScript implementation of the MD5 algorithm:
Key features of our implementation:
- Pure JavaScript MD5 implementation for client-side processing
- Proper UTF-8 text encoding handling
- Real-time hash generation as you type
- Hash comparison and verification functionality
- Security warnings and educational information
Educational Value
Learn About:
- • Hash function principles
- • Cryptographic vulnerabilities
- • File integrity verification
- • Security best practices
Understand:
- • Why MD5 is deprecated
- • Modern hash alternatives
- • Collision attack concepts
- • Proper password hashing