bcrypt Password Hasher & Verifier Tool
Generate secure bcrypt password hashes with customizable salt rounds or verify existing passwords against bcrypt hashes. bcrypt is an adaptive cryptographic hash function specifically designed for password storage, featuring built-in salt generation and configurable work factor for future-proof security.
Operation Mode
bcrypt Algorithm Info
Salt Rounds Configuration
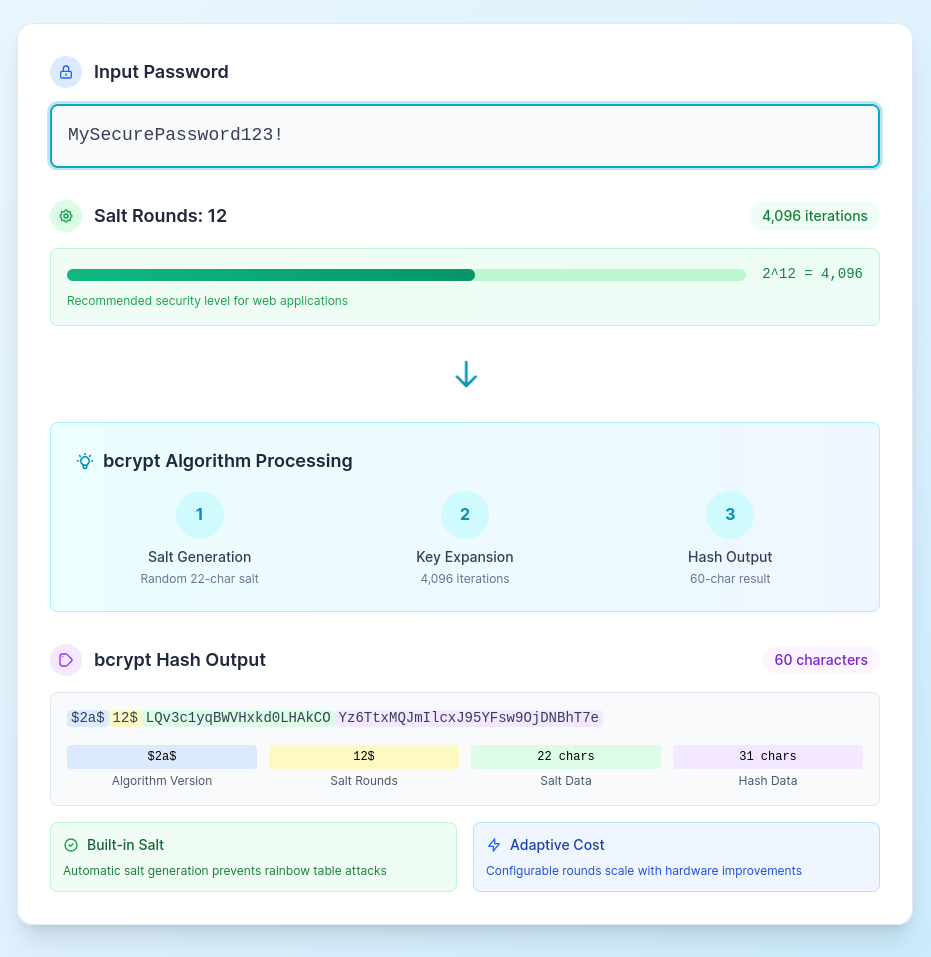
Password
bcrypt Hash
Enter password to generate bcrypt hash
Hash Statistics
Quick Examples
Production-Ready Password Security
bcrypt is the industry standard for secure password storage, specifically designed to protect against modern attack methods and future hardware improvements.
Key Features:
- • Adaptive cost factor (salt rounds)
- • Built-in salt generation and storage
- • Resistance to rainbow table attacks
- • Configurable security-performance balance
Perfect For:
- • User authentication systems
- • Web application login security
- • Database password storage
- • Enterprise security compliance
bcrypt Hash Format
What is bcrypt?
bcrypt is an adaptive cryptographic hash function specifically designed for password hashing. Unlike general-purpose hash functions, bcrypt incorporates a configurable work factor (salt rounds) that makes it computationally expensive and resistant to brute-force attacks as computing power increases.
Key characteristics of bcrypt:
- Adaptive cost: Configurable salt rounds (4-31)
- Built-in salt: Automatic salt generation and storage
- Future-proof: Adjustable difficulty as hardware improves
- Password-specific: Designed exclusively for password storage
- Deterministic output: Same password + salt = same hash
- Fixed format: 60-character string with embedded metadata
Example: "password123" → "$2a$12$R9h/cIPz0gi.URNNX3kh2OPST9/PgBkqquzi.Ss7KIUgO2t0jWMUW"
✅ Password Storage Gold Standard
bcrypt is the recommended choice for password hashing in web applications:
- Industry standard: Used by major frameworks and platforms
- Proven security: Battle-tested against real-world attacks
- Built-in protection: Automatic salt generation prevents rainbow tables
- Adaptive security: Increase rounds as hardware improves
Perfect for user authentication, login systems, and secure password storage.
Features of Our bcrypt Tool:
- Secure hash generation - Production-ready bcrypt implementation
- Password verification - Verify passwords against existing hashes
- Configurable rounds - Adjust salt rounds from 4 to 18
- Password strength analysis - Real-time strength assessment
- Performance estimates - Time cost for different round settings
- Format validation - Verify bcrypt hash format correctness
- Educational examples - Common password demonstrations
- Security best practices - Comprehensive implementation guidance
How to Use the bcrypt Tool
1. Choose Operation Mode
Select "Generate Hash" to create bcrypt hashes from passwords, or "Verify Password" to check a password against an existing bcrypt hash.
2. Configure Salt Rounds
In hash mode, adjust the salt rounds (4-18) based on your security requirements. Higher rounds mean better security but slower processing.
3. Enter Password
Type your password in the input field. The tool will show password strength analysis and generate the hash automatically.
4. Use in Production
Copy the generated hash for use in your application's user database. bcrypt is production-ready and secure for real applications.
Understanding Salt Rounds
| Rounds | Iterations | Estimated Time | Security Level | Use Case |
|---|---|---|---|---|
| 4 | 16 | < 1ms | Basic | Testing only |
| 8 | 256 | ~1ms | Low | Legacy systems |
| 12 | 4,096 | ~10ms | Recommended | Web applications |
| 15 | 32,768 | ~100ms | High | High-security apps |
| 18 | 262,144 | ~1s | Very High | Maximum security |
bcrypt Hash Examples
| Password | Rounds | bcrypt Hash (example) |
|---|---|---|
| password123 | 12 | $2a$12$R9h/cIPz0gi.URNNX3kh2OPST9/PgBkqquzi.Ss7KIUgO2t0jWMUW |
| MySecurePass! | 12 | $2a$12$LQv3c1yqBWVHxkd0LHAkCOYz6TtxMQhmIlcxJ95YFsw9OjDNBhT7e |
| admin | 10 | $2a$10$N9qo8uLOickgx2ZMRZoMyeIjZAgcfl7p92ldGxad68LJZdL17lhWy |
| Tr0ub4dor&3 | 15 | $2a$15$k5UJtE2YFgSK1LgHMSf1mODdJcHxvfI9RdgeEWdNBRXNTGGo/xb/G |
⚠️ Important Notes
- Different salts = different hashes: Same password generates different hashes each time
- Salt is embedded: The hash contains the salt, so you only need to store the hash
- Example hashes above are for demonstration: Actual hashes will be different due to random salts
- Never hardcode hashes: Always generate hashes dynamically in your application
bcrypt Security Applications
Web Applications
- User registration: Hash passwords during signup
- Login authentication: Verify passwords against stored hashes
- Password changes: Generate new hashes for updated passwords
- Admin systems: Secure administrative account passwords
- API authentication: Hash API keys and tokens
- Session management: Secure session token storage
Enterprise Systems
- Employee portals: Secure internal authentication
- Database security: Hash sensitive data fields
- Identity management: LDAP and Active Directory integration
- Compliance requirements: Meet security standards (GDPR, HIPAA)
- Multi-factor auth: Secure backup authentication methods
- Service accounts: Hash automated system passwords
bcrypt vs Other Password Hashing Methods
| Method | Salt Handling | Adaptive Cost | Security | Recommendation |
|---|---|---|---|---|
| Plain Text | None | No | None | Never use |
| MD5 + Salt | Manual | No | Broken | Avoid |
| SHA-256 + Salt | Manual | No | Too Fast | Not Ideal |
| PBKDF2 | Manual | Yes | Good | Acceptable |
| bcrypt | Automatic | Yes | Excellent | Recommended |
| scrypt | Automatic | Yes | Excellent | Good Choice |
| Argon2 | Automatic | Yes | Excellent | Newest Standard |
bcrypt Best Practices
✅ Recommended Practices
- Use 12+ salt rounds: Provides good security-performance balance
- Store only the hash: Never store the original password
- Implement rate limiting: Prevent brute force attacks on login
- Use secure libraries: Don't implement bcrypt yourself
- Regular security audits: Review your authentication code
- Monitor performance: Adjust rounds based on server capacity
💡 Implementation Tips
- Handle async operations: bcrypt hashing is CPU-intensive
- Set appropriate timeouts: Higher rounds take longer
- Use environment variables: Configure rounds per environment
- Test performance: Measure hashing time on your hardware
- Plan for upgrades: Design system to support round increases
- Consider user experience: Balance security with login speed
Related Security Tools
Explore these related security and hashing tools:
Password Generator
Generate strong, secure passwords before hashing them with bcrypt.
Try our Password Generator →SHA-256 Hash Generator
Generate SHA-256 hashes for file integrity and digital signatures.
Try our SHA-256 tool →SHA-512 Hash Generator
Generate SHA-512 hashes for high-security applications.
Try our SHA-512 tool →Text Analysis Tool
Analyze password complexity and character composition.
Try our Text Analysis tool →Frequently Asked Questions
Is bcrypt secure for production applications?
Yes, bcrypt is specifically designed for production password storage and is widely used by major applications. It's considered the gold standard for password hashing.
How many salt rounds should I use?
12 rounds is the current recommended minimum for web applications. Consider 15+ rounds for high-security applications, but test performance impact on your servers.
Why does the same password generate different hashes?
bcrypt automatically generates a random salt for each hash, ensuring that identical passwords produce different hashes. This prevents rainbow table attacks.
Can I increase salt rounds for existing hashes?
You can't modify existing hashes, but you can rehash passwords with higher rounds when users log in, gradually upgrading your security over time.
Is bcrypt better than SHA-256 for passwords?
Yes, bcrypt is specifically designed for passwords with built-in salt and adaptive cost. SHA-256 is too fast and requires manual salt implementation.
What's the maximum password length for bcrypt?
bcrypt has a 72-byte limit for input. Most implementations handle this automatically, but very long passwords may be truncated.
Technical Implementation
Our bcrypt tool implements the algorithm using modern JavaScript with proper security practices:
Key features of our implementation:
- Secure random salt generation using crypto.getRandomValues()
- Proper bcrypt format with version identifier ($2a$)
- Configurable salt rounds with validation (4-18)
- Constant-time comparison for verification
- Comprehensive error handling and validation
Password Security Standard
Production Benefits:
- • Industry-standard password hashing
- • Built-in salt generation and storage
- • Adaptive cost for future-proof security
- • Resistance to rainbow table attacks
Implementation Ready:
- • Framework integration available
- • Scalable performance characteristics
- • OWASP recommended practices
- • Compliance with security standards