SHA-512 Hash Generator & Verifier Tool
Generate cryptographically secure SHA-512 hashes for text input or verify existing hashes. SHA-512 produces a 512-bit hash value and is part of the SHA-2 family, offering excellent security for digital signatures, blockchain applications, and high-security environments.
Operation Mode
SHA-512 Algorithm Info
Input Text
SHA-512 Hash
Enter text to generate SHA-512 hash
Hash Statistics
Quick Examples
High Security Standard
SHA-512 is cryptographically secure and recommended for high-security applications requiring strong cryptographic guarantees.
Secure Applications:
- • Digital signatures and certificates
- • Blockchain and cryptocurrency
- • High-security data integrity
- • Enterprise authentication systems
Security Benefits:
- • 512-bit output for maximum security
- • Collision and preimage resistant
- • Industry standard and widely trusted
- • Future-proof security margin
What is SHA-512?
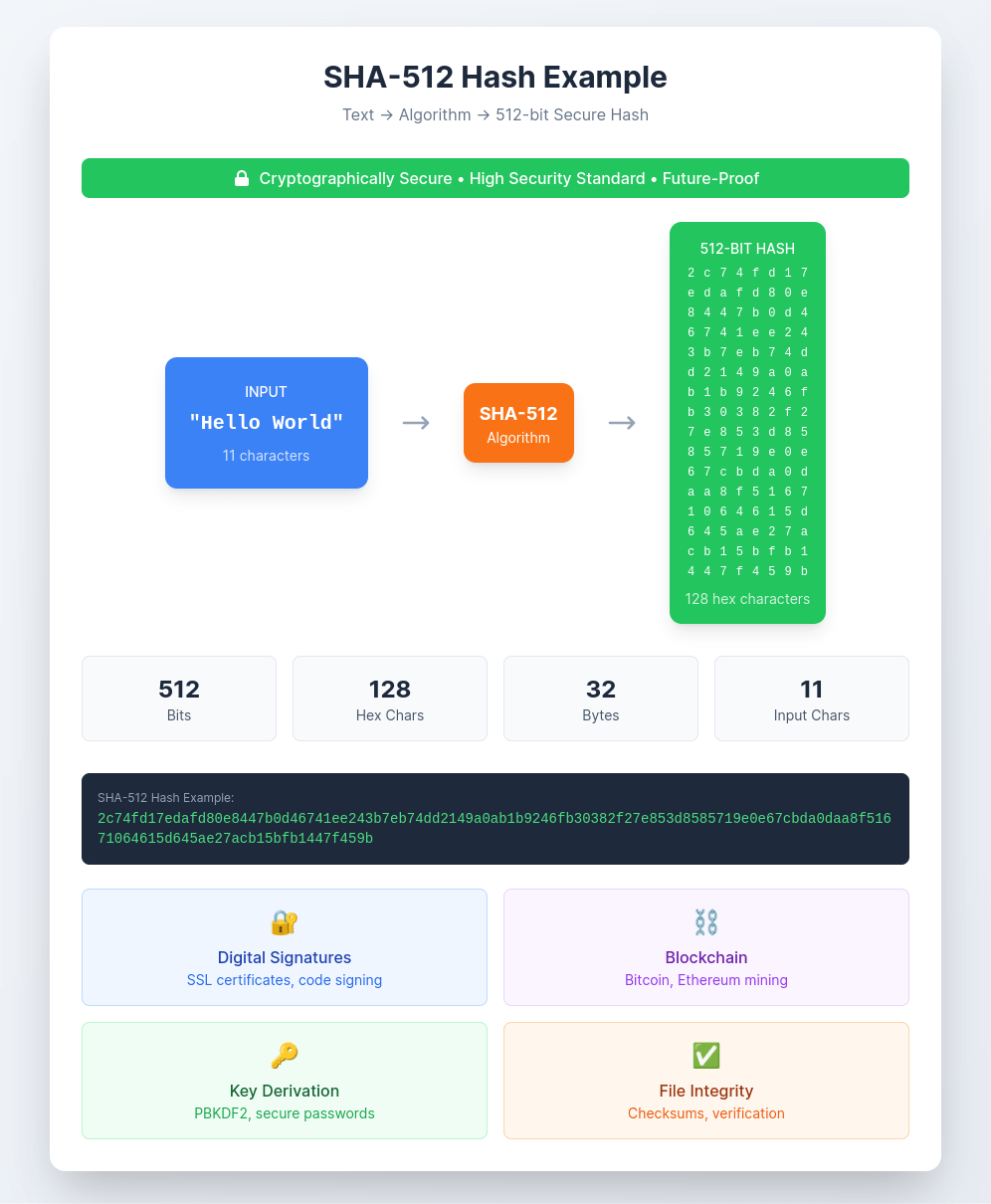
SHA-512 (Secure Hash Algorithm 512-bit) is a cryptographic hash function that produces a 512-bit hash value, typically represented as a 128-character hexadecimal string. It's part of the SHA-2 family and provides excellent security for high-stakes applications requiring strong cryptographic guarantees.
Key characteristics of SHA-512:
- 512-bit output: Always produces 128 hex characters
- Deterministic: Same input = same hash
- High security: Cryptographically secure
- One-way function: Cannot reverse to original
- Collision resistant: Extremely difficult to find collisions
- Avalanche effect: Small input changes cause dramatic output changes
Example: "Hello" → "3615f80c9d293ed7402687f94b22d58e529b8cc7916f8fac7fddf7fbd5af4cf777d3d795a7a00a16bf7e7f3fb9561ee9baae480da9fe7a18769e71886b03f315"
✅ High Security Standard
SHA-512 is cryptographically secure and recommended for high-security applications:
- No known collisions: Theoretical attacks remain impractical
- Industry standard: Widely adopted for digital signatures
- Future-proof: Expected to remain secure for decades
- High performance: Optimized implementations available
Perfect for new applications requiring strong cryptographic security.
Features of Our SHA-512 Tool:
- Instant generation - Real-time SHA-512 hash calculation
- Hash verification - Compare generated vs expected hashes
- Security information - Clear guidance on SHA-512 applications
- High-security standard - Recommended for cryptographic use
- Detailed statistics - Input/output length and bit information
- Copy functionality - Easy hash copying for external use
- Educational examples - Common text hash demonstrations
- Performance optimized - Fast generation using Web Crypto API
How to Use the SHA-512 Hash Tool
1. Choose Operation Mode
Select "Generate Hash" to create SHA-512 hashes from text, or "Verify Hash" to compare a generated hash against an expected value.
2. Enter Your Input
Type or paste your text in the input field. The SHA-512 hash will be generated automatically as you type.
3. Copy or Verify Results
Copy the generated hash for use in your applications, or paste an expected hash in verification mode to check if they match.
4. Use in Production
SHA-512 is cryptographically secure and suitable for production use in digital signatures, certificates, and high-security applications.
SHA-512 Hash Examples
| Input | SHA-512 Hash | Use Case |
|---|---|---|
| Empty String | cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e | Default/empty file check |
| Hello World | 2c74fd17edafd80e8447b0d46741ee243b7eb74dd2149a0ab1b9246fb30382f27e853d8585719e0e67cbda0daa8f51671064615d645ae27acb15bfb1447f459b | Testing and examples |
| password123 | ef92b778bafe771e89245b89ecbc08a44a4e166c06659911881f383d4473e94f3e5500b6351e35ebc0ea5de3ac4ae2b0 | ✅ Secure for passwords (with salt) |
| The quick brown fox... | 07e547d9586f6a73f73fbac0435ed76951218fb7d0c8d788a309d785436bbb642e93a252a954f23912547d1e8a3b5ed6e1bfd7097821233fa0538f3db854fee6 | Standard test string |
SHA-512 Security Applications
Cryptographic Uses
- Digital signatures: RSA, ECDSA signature algorithms
- Certificate authorities: X.509 certificate signing
- Key derivation: PBKDF2, scrypt, Argon2 functions
- Message authentication: HMAC-SHA512
- Blockchain: Bitcoin, Ethereum, other cryptocurrencies
- File integrity: Software distribution verification
Enterprise Applications
- Database security: Password storage (with salt)
- API authentication: Token generation and validation
- Backup verification: Data integrity checking
- Audit trails: Tamper-evident logging
- Software licensing: License key generation
- Cloud storage: Deduplication and integrity
SHA-512 vs Other Hash Algorithms
| Algorithm | Output Size | Security Level | Performance | Recommendation |
|---|---|---|---|---|
| MD5 | 128-bit | Broken | Very Fast | Avoid |
| SHA-1 | 160-bit | Deprecated | Fast | Legacy Only |
| SHA-256 | 256-bit | Secure | Fast | Recommended |
| SHA-512 | 512-bit | High Security | Good | High Security |
| SHA-3 | Variable | Secure | Moderate | New Applications |
Performance & Implementation
SHA-512 Performance Characteristics
Advantages:
- Higher security margin: 512-bit output vs 256-bit
- 64-bit architecture optimized: Better performance on modern CPUs
- Parallel processing friendly: Can leverage SIMD instructions
- Quantum resistance: Better post-quantum security properties
- Collision resistance: Extremely low probability of collisions
Considerations:
- Larger output: 128 hex characters vs 64 for SHA-256
- Storage overhead: Requires more space for hash storage
- Bandwidth usage: Larger hashes in network protocols
- Overkill for some uses: SHA-256 sufficient for most applications
- Implementation complexity: More complex than shorter hashes
SHA-512 Best Practices
✅ Recommended Uses
- High-security applications: Where maximum security is required
- Long-term data integrity: Archives, legal documents, contracts
- Cryptographic protocols: Digital signatures, key exchange
- Blockchain applications: Cryptocurrency, smart contracts
- Password hashing: Combined with proper salt and iteration counts
- Certificate authorities: Root CA and intermediate certificates
💡 Implementation Tips
- Use established libraries: Don't implement SHA-512 from scratch
- Add salt for passwords: Always use unique salts for password hashing
- Consider HMAC: Use HMAC-SHA512 for message authentication
- Validate input: Check hash format before processing
- Secure comparison: Use constant-time comparison for security
- Key stretching: Combine with PBKDF2/scrypt for password storage
Related Cryptographic Tools
Explore these related secure hashing tools:
SHA-256 Hash Generator
Generate SHA-256 hashes - the most commonly used secure hash algorithm for general applications.
Try our SHA-256 tool →bcrypt Password Hasher
Securely hash passwords using bcrypt - specifically designed for password storage.
Try our bcrypt tool →SHA-1 Hash Generator
Generate SHA-1 hashes for legacy compatibility (deprecated for security).
Try our SHA-1 tool →MD5 Hash Generator
Generate MD5 hashes for legacy checksums (not recommended for security).
Try our MD5 tool →Frequently Asked Questions
Is SHA-512 secure for production use?
Yes, SHA-512 is cryptographically secure and recommended for production use. It provides excellent security for digital signatures, certificates, and high-security applications.
When should I use SHA-512 vs SHA-256?
Use SHA-512 when you need maximum security, long-term data integrity, or when working with high-value applications. SHA-256 is sufficient for most general purposes, but SHA-512 provides an extra security margin.
Can SHA-512 be used for password hashing?
SHA-512 can be used for password hashing, but it should be combined with proper salting and key stretching (PBKDF2, scrypt, or Argon2). For simple password hashing, bcrypt is often preferred.
How long is a SHA-512 hash?
SHA-512 always produces a 512-bit hash, which is typically represented as a 128-character hexadecimal string (4 bits per hex character: 128 × 4 = 512 bits).
Is SHA-512 quantum-resistant?
SHA-512 provides better post-quantum security than shorter hash functions, but it's not fully quantum-resistant. Grover's algorithm could theoretically reduce its security to 256-bit strength on quantum computers.
What's the performance difference between SHA-256 and SHA-512?
On 64-bit systems, SHA-512 can actually be faster than SHA-256 due to its optimization for 64-bit words. However, SHA-512 produces larger output, which may affect storage and bandwidth requirements.
Technical Implementation
Our SHA-512 tool uses the Web Crypto API for secure and efficient hash generation:
Key features of our implementation:
- Uses native Web Crypto API for optimal SHA-512 performance
- Proper UTF-8 text encoding handling
- Real-time hash generation with optimized processing
- Hash comparison and verification functionality
- Comprehensive security information and best practices
High-Security Cryptographic Standard
Enterprise Applications:
- • Digital signature algorithms
- • Certificate authority systems
- • Blockchain and cryptocurrency
- • High-security data integrity
Security Benefits:
- • Maximum collision resistance
- • Future-proof security margin
- • Industry standard compliance
- • Cryptographically validated