Rail Fence Cipher: Zigzag Transposition Encryption Tool
The Rail Fence cipher is a transposition cipher that writes the message in a zigzag pattern across multiple "rails" or lines, then reads off the cipher text row by row. This creates a simple but effective method of scrambling text that was historically used for secure communication.
Operation Mode
Rail Configuration
Input Text
Rail Fence Result
Enter text to see Rail Fence conversion
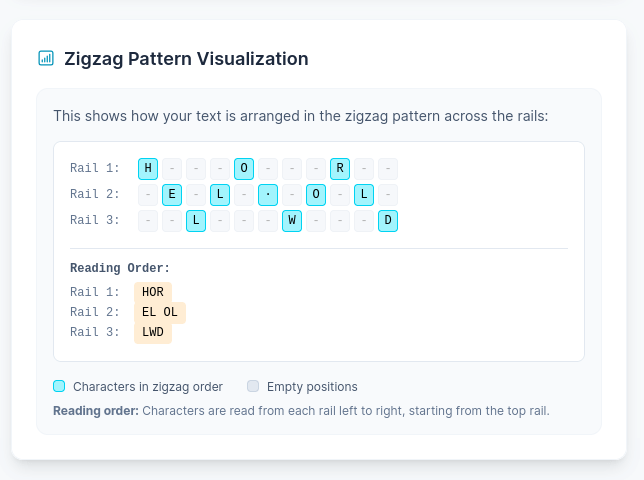
Zigzag Pattern Visualization
Cipher Statistics
Quick Examples
About the Rail Fence Cipher
The Rail Fence cipher is a transposition cipher that arranges text in a zigzag pattern across multiple rails (lines), then reads the result row by row. It's a classic example of how simple rearrangement can obscure text.
How it works:
- • Write text in zigzag pattern
- • Bounce between top and bottom rails
- • Read each rail left to right
- • Combine all rails for result
Key Features:
- • Transposition (rearrangement) cipher
- • Visual zigzag pattern
- • Configurable complexity (rails)
- • Educational and historical value
What is the Rail Fence Cipher?
The Rail Fence Cipher is a transposition cipher that arranges the plaintext in a zigzag pattern across multiple horizontal lines called "rails". The message is written diagonally across the rails, bouncing between the top and bottom rails, then the ciphertext is created by reading each rail from left to right.
Key characteristics:
- Transposition: Rearranges letters, doesn't substitute
- Zigzag pattern: Creates a fence-like structure
- Configurable rails: More rails = more complexity
- Visual pattern: Easy to see the encryption process
Example with 3 rails: "HELLO WORLD" becomes "HOLELWLORD"
Features of Our Rail Fence Cipher Tool:
- Interactive rail adjustment - Choose 2-10 rails with slider control
- Real-time processing - See results as you type or adjust rails
- Visual pattern display - Interactive zigzag pattern visualization
- Pattern analysis - Shows reading order and character positions
- Dual operation - Encrypt and decrypt with the same interface
- Character preservation - Handles spaces and special characters
- Educational visualization - Learn how the cipher works step by step
- Mobile-responsive design - Works perfectly on all devices
How to Use the Rail Fence Cipher Tool
1. Choose Operation Mode
Select "Encrypt" to encode your message or "Decrypt" to decode a Rail Fence encrypted message. Make sure to use the same number of rails for both operations.
2. Set Number of Rails
Use the slider to choose between 2-10 rails. More rails create more complex patterns but may be harder to decrypt manually. 3-4 rails are most commonly used.
3. Enter Your Text
Type or paste your message. The tool will automatically create the zigzag pattern and show you the visual representation of how the cipher works.
4. Analyze the Pattern
Study the visual pattern to understand how the Rail Fence cipher arranges your text. This helps in learning the encryption process.
How Rail Fence Cipher Works
Encryption Process
The encryption process follows these steps:
- Write the plaintext in a zigzag pattern across the specified number of rails
- Start at the top rail and move diagonally down
- When you reach the bottom rail, bounce back diagonally up
- Continue this zigzag pattern until all letters are placed
- Read the ciphertext by reading each rail from left to right, top to bottom
Example with "HELLO WORLD" and 3 Rails
Practical Examples
| Original Text | Rails | Encrypted Text |
|---|---|---|
| HELLO | 2 | HLOEL |
| HELLO | 3 | HOELL |
| HELLO WORLD | 3 | HOREL OLLWD |
| RAILFENCE | 3 | RFEALECIN |
Security Analysis
The Rail Fence cipher provides limited security by modern standards, but it has some interesting characteristics:
Strengths
- Simple to implement and understand
- No key distribution required (just rail count)
- Scrambles text without letter substitution
- Visual pattern makes it educational
- Can be combined with other ciphers
- Works with any text length
Weaknesses
- Very weak against modern cryptanalysis
- Limited key space (only rail count varies)
- Pattern becomes obvious with longer texts
- Frequency analysis still possible
- Vulnerable to brute force (few possible rails)
- No protection against statistical attacks
Historical Usage and Variations
The Rail Fence cipher has been used throughout history in various forms:
Historical Applications
- Ancient Greece: Used by Spartan military for field communications
- Civil War: Employed by both Union and Confederate forces
- World War I: Used for tactical field messages
- Telegraph era: Popular for commercial message security
Modern Variations
- Offset Rail Fence: Starting at different rail positions
- Variable Rails: Changing rail count throughout the message
- Combined Ciphers: Rail Fence + substitution ciphers
- Reverse Reading: Reading rails in different orders
Modern Uses for Rail Fence Cipher
While not suitable for serious security, the Rail Fence Cipher has several modern applications:
- Educational tool for learning transposition cipher concepts
- Puzzle creation and recreational cryptography
- Programming exercises and algorithm implementation
- Basic obfuscation for non-sensitive data
- Children's coding games and activities
- Historical cryptography demonstrations
- Pattern recognition exercises
- Introduction to encryption concepts
Security Notice: The Rail Fence Cipher should not be used for protecting sensitive information in modern applications. It's easily broken and provides minimal security.
Related Cipher Methods
If you're interested in the Rail Fence Cipher, explore these related cryptographic techniques:
Caesar Cipher
A substitution cipher that shifts letters by a fixed number. Often combined with Rail Fence for added complexity.
Try our Caesar Cipher tool →Vigenère Cipher
A polyalphabetic substitution cipher that can be combined with Rail Fence for layered encryption.
Try our Vigenère Cipher tool →Frequently Asked Questions
How many rails should I use?
For most purposes, 3-4 rails provide a good balance of complexity and usability. More rails create more complex patterns but may be harder to decrypt manually. The maximum effective rails is roughly half the message length.
Can Rail Fence handle spaces and punctuation?
Yes, our implementation preserves all characters including spaces, punctuation, and numbers. They are treated as regular characters in the zigzag pattern.
Is Rail Fence secure for real communications?
No, Rail Fence provides very limited security and can be easily broken with modern techniques. It should only be used for educational purposes, puzzles, or simple obfuscation.
How do I decrypt a Rail Fence message?
To decrypt, you need to know the number of rails used. Our tool handles this automatically - just select "Decrypt" mode and enter the same rail count used for encryption.
Can I combine Rail Fence with other ciphers?
Yes! Rail Fence is often combined with substitution ciphers like Caesar or Vigenère to create layered encryption. Apply one cipher first, then the other to the result.
Algorithm Implementation Details
The Rail Fence cipher algorithm can be broken down into clear steps:
Encryption Algorithm:
- Create an array of empty rails (rows)
- Initialize position at top rail, direction = down
- For each character: place on current rail, then move
- At top/bottom rails: reverse direction
- Concatenate all rails left-to-right to form ciphertext
Decryption Algorithm:
- Create rail pattern marking character positions
- Fill marked positions with ciphertext characters rail by rail
- Read the filled rails in zigzag pattern
- Reconstruct original text following the fence path