Autokey Cipher: Self-Extending Key Encryption Tool
The Autokey Cipher is an improvement over the Vigenère Cipher that eliminates key repetition by using the plaintext itself to extend the key. This makes it significantly more secure against frequency analysis and pattern detection attacks while maintaining the polyalphabetic substitution principle.
Operation Mode
Initial Keyword
Key Extension
Input Text
Output Result
Enter keyword and text to see results
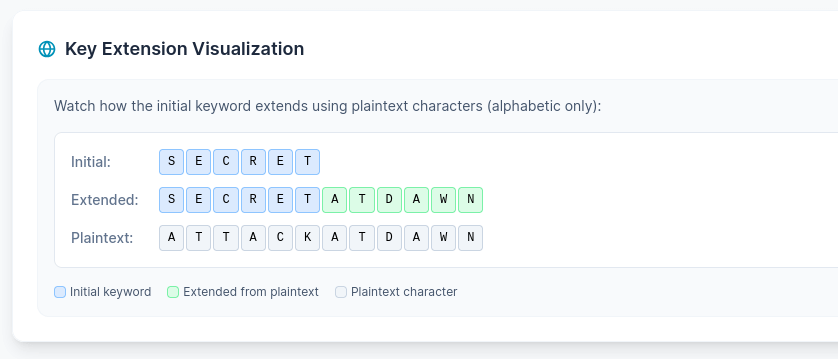
Key Extension Visualization
Autokey vs. Vigenère Comparison
Autokey Cipher
No repetition pattern
- ✓ Key extends with plaintext
- ✓ No repeating patterns
- ✓ Unique key for each position
- ✓ More secure against analysis
Vigenère Cipher
Repeating pattern
- • Fixed key length
- • Key repeats throughout
- • Predictable patterns
- • Vulnerable to period analysis
Encryption Statistics
Quick Examples
What is the Autokey Cipher?
The Autokey Cipher is a polyalphabetic substitution cipher that was invented by Blaise de Vigenère in 1586. It's an improvement over the standard Vigenère Cipher that eliminates the main weakness of repeating keys by using the plaintext itself to extend the initial keyword.
How it works:
- Initial keyword: "SECRET"
- Plaintext: "ATTACK AT DAWN"
- Extended key: "SECRET ATTACK"
- The plaintext extends the key, eliminating repetition
This creates a unique encryption pattern for each message, making cryptanalysis much more difficult.
Features of Our Autokey Cipher Tool:
- Real-time encryption/decryption - See results as you type
- Self-extending key visualization - Watch how the key grows with plaintext
- Security analysis - Compare with Vigenère cipher security
- Key pattern display - Visual representation of key extension
- Case preservation - Maintains original capitalization
- Educational insights - Learn why Autokey is more secure
- 100% client-side processing - Your data never leaves your browser
- Mobile-responsive design - Works perfectly on all devices
How to Use the Autokey Cipher Tool
1. Choose Your Operation
Select "Encrypt" to encode your message or "Decrypt" to decode an encrypted message. The same initial keyword must be used for both operations.
2. Enter Your Initial Keyword
Choose a keyword that will start the encryption process. Unlike Vigenère, this keyword won't repeat - it will be extended by the plaintext itself.
3. Input Your Text
Type or paste the text you want to encrypt or decrypt. Watch how the key extends automatically using the plaintext characters.
4. Analyze the Key Extension
Observe how the initial keyword is extended with plaintext characters, creating a unique key that never repeats.
Practical Examples of Autokey Cipher
| Plaintext | Initial Key | Extended Key | Ciphertext |
|---|---|---|---|
| ATTACK AT DAWN | SECRET | SECRETATTACK | SXVRGK EX DWTR |
| HELLO WORLD | KEY | KEYHELLOWOR | RSPPS ASENH |
| CRYPTOGRAPHY | CIPHER | CIPHERCRYPTOGR | EAFKXKMTCRPI |
Autokey vs. Vigenère Cipher
The Autokey Cipher addresses the main weakness of the Vigenère Cipher: key repetition. Here's how they compare:
Autokey Advantages
- No key repetition - each character uses unique key
- Resistant to Kasiski examination
- More secure against frequency analysis
- Self-synchronizing in some implementations
- Harder to break with statistical methods
- Key length matches message length
Vigenère Characteristics
- Fixed key repeats throughout message
- Vulnerable to Kasiski examination
- Pattern analysis can reveal key length
- Simpler to implement manually
- More predictable key structure
- Key length independent of message
Security Analysis
The Autokey Cipher provides significantly enhanced security compared to simple polyalphabetic ciphers:
Strengths
- No key repetition: Each position uses a unique key character
- Variable key length: Key extends to match message length
- Self-modifying: Key depends on the message content
- Resistant to period analysis: No repeating patterns to exploit
Limitations
- Still vulnerable to known plaintext attacks
- Initial keyword must remain secret
- Not suitable for modern sensitive data
- Error propagation in manual implementation
Historical Context and Development
The Autokey Cipher was invented by Blaise de Vigenère in 1586, though it's often confused with the simpler repeating-key cipher that bears his name. Vigenère actually considered the autokey version superior due to its enhanced security properties.
Key historical points:
- 1586: Invented by Blaise de Vigenère in "Traicté des Chiffres"
- 16th-17th centuries: Used in diplomatic communications
- 19th century: Analyzed by cryptographers like Babbage and Kasiski
- World War era: Influenced development of more complex ciphers
- Modern era: Studied for educational and historical purposes
Autokey Cipher Variants
Several variants of the Autokey Cipher have been developed over time:
Autokey (Plaintext)
Uses the plaintext to extend the key - the most common and secure variant.
Autokey (Ciphertext)
Uses the ciphertext to extend the key - less secure but self-synchronizing.
Progressive Key
Key characters are modified arithmetically as they're used.
Mixed Autokey
Combines multiple extension methods for enhanced complexity.
Modern Applications and Learning
While not suitable for protecting sensitive data in the digital age, the Autokey Cipher serves important educational purposes:
- Cryptography education: Demonstrates key extension principles
- Historical study: Understanding classical cipher evolution
- Algorithm design: Concepts applicable to modern cryptography
- Security analysis: Learning about vulnerability assessment
- Puzzle creation: Advanced cryptographic challenges
- Academic research: Foundation for studying cipher improvements
Security Notice: While more secure than basic polyalphabetic ciphers, the Autokey Cipher should not be used for protecting sensitive information in modern applications.
Related Encryption Methods
Explore these related cryptographic techniques to deepen your understanding:
Vigenère Cipher
The foundation cipher that Autokey improves upon - learn the basic polyalphabetic principles.
Try our Vigenère Cipher tool →Caesar Cipher
The simple substitution cipher that forms the basis of all polyalphabetic ciphers.
Try our Caesar Cipher tool →Frequently Asked Questions
How is Autokey different from Vigenère?
The key difference is that Autokey uses the plaintext itself to extend the initial keyword, eliminating the repeating key pattern that makes Vigenère vulnerable to cryptanalysis.
Is the Autokey Cipher secure?
While much more secure than Vigenère, it's still not suitable for modern sensitive data protection. It can be broken with sufficient ciphertext and computational resources.
What happens if I make an error during manual decryption?
Manual decryption errors can propagate through the rest of the message since each decrypted character becomes part of the key for subsequent characters.
Can I use spaces and punctuation in the plaintext?
Our tool handles spaces and punctuation by leaving them unchanged and not including them in the key extension, focusing only on alphabetic characters.
Why was the Autokey Cipher invented?
It was created to address the main weakness of repeating-key ciphers: the pattern created by key repetition that made them vulnerable to frequency analysis and period detection.
How the Algorithm Works
The Autokey Cipher algorithm follows these steps:
The key insight is that each alphabetic character of the plaintext becomes part of the key for encrypting subsequent characters, creating a unique key stream that never repeats.